Privacy is not the enemy. But indifference to complexity is.
By Mike Masoud and The American Anti-Corruption Institute (AACI)
July 22, 2025
As regulators focus on catching up, criminals have already mastered the art of exploiting digital loopholes. The narrative that “blockchains are fully traceable” is outdated and misleading. In reality, launderers now blend decentralized tools, obscure wallets, and cross-chain bridges to outrun traditional controls.
At The American Anti-Corruption Institute (AACI), we believe that every regulator, prosecutor, compliance officer, auditor, and banking executive should understand this shift. Not through hype or fearmongering, but through clarity.
A new laundering lifecycle
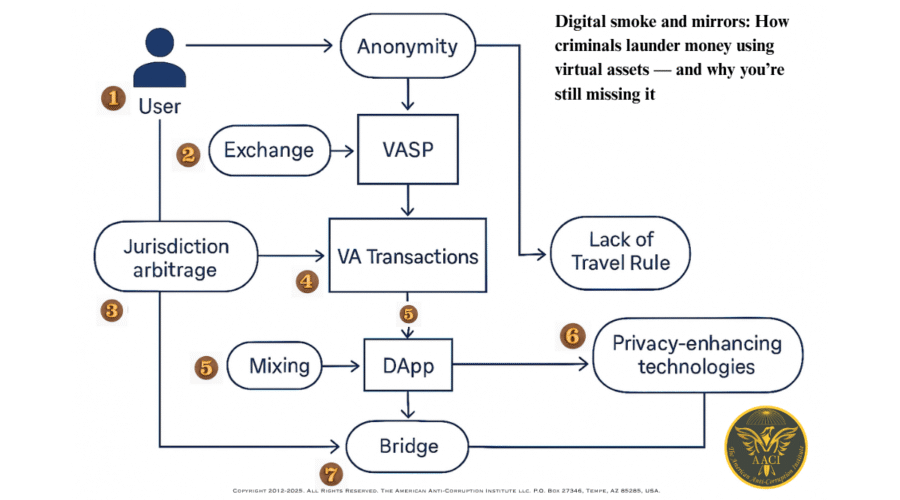
Here’s how criminals do it in 7 simplified steps:

1. Entry via VASPs: A user enters the crypto ecosystem through a Virtual Asset Service Provider (VASP) like an exchange or broker. Weak KYC here is a green light for illicit actors.
2. Jurisdiction arbitrage: They register in one country, transact from another, and send documents from a third, leveraging inconsistent AML standards globally.
3. Blockchain layering: Crypto is split, mixed, and moved on-chain using short-lived wallets and complex transfer paths that make attribution difficult.
4. DeFi obfuscation: Funds move through decentralized exchanges, NFT platforms, and lending pools, with no compliance officers in sight.
5. Privacy tools: Mixers, stealth addresses, and privacy coins break traceability. Even the best analytics hit a wall here.
6. Cross-chain bridges: Assets jump from Ethereum to Tron to Solana to Binance Smart Chain, each hop escaping a single compliance perimeter.
7. Exit: Funds return as stablecoins, prepaid cards, or fiat via P2P or OTC desks, cleaned and difficult to trace.
Why it matters
a. Auditors often miss the crypto inflows behind clean balance sheets.
b. Bankers accept deposits from crypto off-ramps without assessing risk.
c. Prosecutors struggle to build solid cases without early KYC preservation.
d. Regulators still treat developers and protocol operators as outside their scope.
This isn’t about blaming innovation. It’s about understanding risk without simplification.
Read the full breakdown
This blog post is only a primer. The full article, complete with diagram, real red flags, and critical questions for institutions, is available on our Substack.
We invite you to read, subscribe, and share it with peers who must stay ahead of digital laundering risks.
The American Anti-Corruption Institute (AACI) Together, Empowering Tone at the Top.